I decided to learn more about log management, how to track down incidents, and how to extract useful information from large amounts of data(logs). The reason for this setup is so that eventually I can create a honeypot environment and I would like to have a single repository to pull information from.
I set Graylog up on a QEMU/KVM Virtual Machine running CentOS 7. Initially I gave the VM 1GB of RAM and a 4 core vCPU. This may change later, depending on how many logs are being received. I just used the minimal CentOS install since we will be installing all other resources as we need them.
I’m not going to go into setting up Graylog here, as they have fantastic documentation on setting it up for RHEL/CentOS here:
Notes on setup:
- Since I am not running this in a production environment, I saved myself some headache and disabled SELinux.
- I had trouble installing the Graylog Repo directly to the server. In order to fix that I downloaded the RPM manually and transferred the .rpm via SCP to the server.
- Remember to set up a static IP!
Please thoroughly follow the instructions in that guide! They do a much better job at explaining things than I can.
First thoughts:
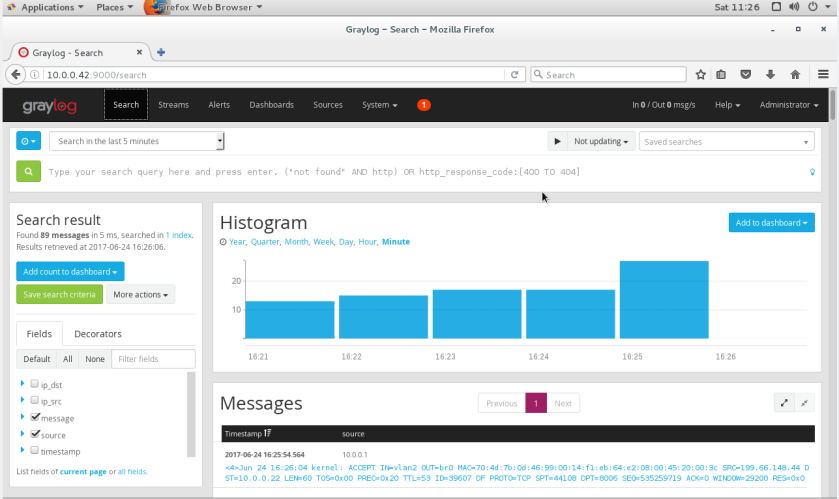
The Web Interface is super nice.
There are a ton of features, the search function is extremely powerful, and it allows you to pull specific fields from your log messages and do all sorts of cool things with them. Once we have logs anyway… (This image is deceiving, I had already had some logs being forwarded at this time)
Getting Logs into our server
First, if you’re using an OS with a firewall (which I hope you are!!!!!) open the port that you’ll be using for log traffic.
Then read this, once again, their documentation is fantastic and goes over most of this in details:
http://docs.graylog.org/en/2.2/pages/sending_data.html
Basically the process goes something like this:
- Create an input
- Start input
- Forward logs from X server via whichever method you used to create the input to the port you specified (and opened in your firewall!)
- Check your log server and see if logs are coming in!
Parsing data
This is where I am currently at. I now have logs coming in from my router, VM host, and a few windows machines but haven’t created any extractors for them yet. So I have some raw messsages that I have to do some very explicit searching for, which isn’t tooo bad but you can’t make a ton of cool graphs and stuff with it yet..
This article explains extractors and how to create them nicely:
http://docs.graylog.org/en/2.2/pages/extractors.html
I’ll update more once I get some message extracting done!
